Beast's Domain Mac OS
Beast's Domain Mac Os Catalina
Currently seeking micro/ tiny apartment opportunities! Hi Guys Welcome to elearninginfoit my name is rajesh i just inform about this video only for Training,Tutorials and Education purpose More information about.

Wiki Mac Os
I have Mac OS X clients bound to an AD domain right now. We are migrating to a new domain. The 2 AD domains are up and running in production now. They are not in the same forest, but rather they are independent forests themselves. The 2 AD domains have a full trust between themselves. By the end of the year the old AD domain will be deprecated and removed.
There will be an interim period where some of our file servers & storage will live in the new domain before all my users are migrated. While users can resolve the new file servers in the new domain via DNS, I cant get Kerberos to work for those servers. Thus users are challenged to authenticate manually.
My Mac OS X clients are bound to the primary AD domain (lets call it domain A).
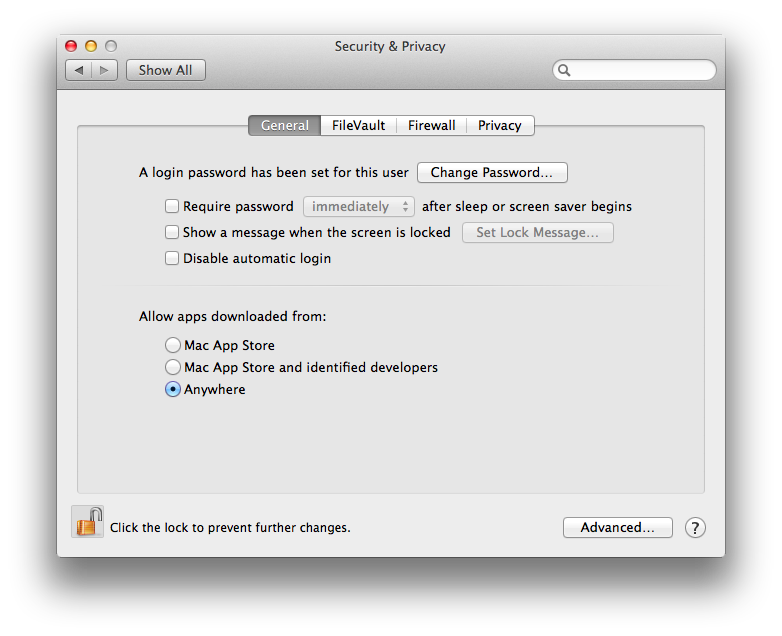
'Allow authentication from any domain in the forest' is enabled in the DS GUI Utility. I dont see any magic options in the dsconfigad command line utility. the 'namespace' switch looks interesting, but I can find an example of how to use it.
I can ping and resolve all hosts in Domain B. DNS is not an issue.
All servers in both domains point to the the same NTP time servers. No time drifting here.
The DCs in both Domain A and Domain B are KDCs and each domain has a Kerberos realm for its own domain. Not sure if this is default settings or not.
I am getting a valid TGT from the DCs in Domain A as expected.
I have a mix of 10.5.8 and 10.6.4 Macs in production. They behave exactly the same.
All user accounts still live in Domain A. They have not been migrated or moved to Domain B yet. Same for the computer records in AD.
I noticed that right now the TGT I get from the KDC/DC in Domain A is not fordwarable. Not sure what this means.
I can manually reuest a TGT from both realms/domains via the Apple Ticket Viewer utility.
Kerberos works fine for all services in domain A from my Macs. Kerberos does not work when connecting to servers in Domain B.
I have a Mac bound to Domain B too for testing. It has the exact opposite problem: Kerberos works fine for all services in domain B from Mac bound to Domain B. But Kerberos does not work when conencting to servers in Domain A from Domain B.
All my Windows PCs and Linux PCs in Domain A are able to get Kerberized services to work just fine in both domains - no problems. The Mac clients are the only systems having issues with Kerberos/SSO.
Im wondering if Mac OS isn't understanding or honoring the dual-AD domain trust for some reason. Obviously I cant bind to 2 different domains.
Possible ideas:
Build 1 Kerberos realm for both domains and not have 2 realms? Im not sure is Windows DC servers can do this or not. Not sure how MS KDC severs work in AD.
Tell Kerberos on the Mac clients to be able to forward their TGT to other realms/domains when connecting to Kerberized services?
Enable some sort of namespace support in the DS plugin? I cant find an example of how to do this correctly.